Web Application and Penetration Testing

DOI:
https://doi.org/10.54060/JIEEE/001.02.003Keywords:
Web application, Penetration testing, OWASPAbstract
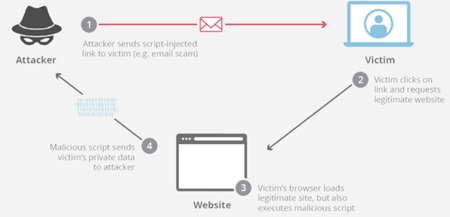
In the present scenario, the usage of internet is enormous and is escalating day by day. Internet facilities are employed in almost every field of work and people are becoming depending on it, with the increasing dependency on the internet, concern regarding information security has been increased. Because most of the work, e-commerce, chatting, payment of the bill, etc. are work through over the internet. That is why security is most important for any web site. Basically, such security concern is high in the field of organizations, institutions, and the financial sector. This paper aims to address the top most vulnerability concerns and how to overcome them. This paper addresses most of the popular vulnerabilities, which are amongst the top 10 according to OWASP and addresses the precautions to be taken to deal with these vulnerabilities. This paper provides a better understanding in a simple and easy way. When the entire world is behind new technologies and everything is moving towards the internet, the need for security increases. One has to be sure about the security of their website as well as the security and privacy of the end users. So, when the world is demanding for new technologies there will be an increase in demand for security testing. Every application or website is considered good only when it is secure and it can only be done by a web tester. This paper explores the vulnerabilities in a precise manner.
Downloads
References
S. Kumar, R. Mahajan, N. Kumar, et al, “A study on web application security and detecting security vulnerabilities,” in 6th International Conference on Reliability, Infocom Technologies and Optimization (Trends and Future Directions) (ICRITO) pp. 451-455. Sept. 2017.
N. Antunes and M. Vieira, “Enhancing penetration testing with attack signatures and interface monitoring for the detection of injection vulnerabilities in web services,” in IEEE International Conference on Services Computing, pp. 104-111, July 2011.
P. S. Shinde and S. B. Ardhapurkar, “Cyber security analysis using vulnerability assessment and penetration testing,” in World Conference on Futuristic Trends in Research and Innovation for Social Welfare (Startup Conclave), pp. 1-5, March 2016,
J. Fonseca, M. Vieira, and H. Madeira, “Testing and comparing web vulnerability scanning tools for SQL injection and XSS attacks,” in 13th Pacific Rim International Symposium on Dependable Computing (PRDC), pp. 365-372, Dec. 2007.
Y. Stefinko, A. Piskozub, and R. Banakh, “Manual and automated penetration testing. Benefits and drawbacks. Modern tendency,” in 13th International Conference on Modern Problems of Radio Engineering, Telecommunications and Computer Science (TCSET), pp.488-491, Feb. 2016