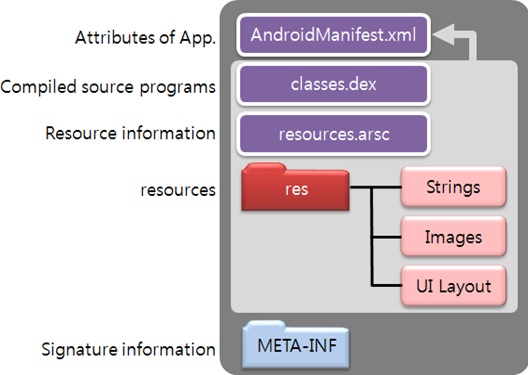
Vulnerabilities in Android OS and Security of Android Devices

DOI:
https://doi.org/10.54060/JIEEE/003.01.004Keywords:
Vulnerabilities, Android Security, Smartphone, Security, AttacksAbstract
The number of malicious mobile and android based application targeting Android users and their smartphones has increase at a fast rate. In addition, these malicious harms causing application are powerful enough to download modules from remote servers which are usually run by malicious infectors, due to which unexpected events can be triggered inside the smartphones. Then, the attacker gets control and hold on the per-sonal and private information and data which is stored within the person’s smartphone illegally.
Downloads
References
“Mobile Phone Tracker,” IDC: The premier global market intelligence company. [Online]. Available: https://www.idc.com/getdoc.jsp?containerId=TEA004804. [Accessed: 28-Mar-2022].
S. Seo, D. Lee and K. Yim, "Analysis on Maliciousness for Mobile Applications," 2012 Sixth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, 2012, pp. 126-129, doi: 10.1109/IMIS.2012.190.
M. Diaz et al., “Technology news, analysis, comments and product reviews for IT professionals,” ZDNet. [Online]. Available: https://www.zdnet.com/. [Accessed: 28-Mar-2022].
A. Singh and P. Singh and A. K. Tiwari, “A Comprehensive Survey on Machine Learning,” Journal of Management and Ser-vice Science, vol. 1, no. 1, pp. 1–17, 2021.
N. Srivastava, U. Kumar, and P. Singh, “Software and Performance Testing Tools,” Journal of Informatics Electrical and Electronics Engineering (JIEEE), vol. 2, no. 1, pp. 1–12, 2021.
“Gartner says worldwide smartphone sales declined 5% in fourth quarter of 2020,” Gartner. [Online]. Available: https://www.gartner.com/en/newsroom/press-releases/2021-02-22-4q20-smartphone-market-share-release. [Accessed: 28-Mar-2022].
W. Enck, M. Ongtang, and P. McDaniel. Mitigating Android Software Misuse Before It Happens. Technical Report NAS-TR-00942008, Network and Security Research Center, Department of Computer Science and Engineering, Pennsylvania State University, University Park, PA, USA, November 2008.
Thomas Blasing, Aubrey-Derrick Schmidt, Leonid Batyuk, Seyit A. Camtepe, and Sahin Albayrak. An android application sandbox system for suspicious software detection. 5th International Conference on Malicious and Unwanted Software (Malware 2010), Nancy, France, 2010.
A. Singh, P. Singh, “Image Classification: A Survey. Journal of Informatics Electrical and Electronics Engineering”, vol. 01, Iss. 02, S. no. 2, pp. 1-9, 2020.
S. Kumar, P. K. Srivastava, G. K. Srivastava, P. Singhal, D. Singh, and D. Goyal, “Chaos based image encryption security in cloud computing,” J. Discrete Math. Sci. Cryptogr., vol. 25, no. 4, pp. 1041–1051, 2022.
N. Srivastava, U. Kumar and P. Singh (2021) Software and Performance Testing Tools. Journal of Informatics Electrical and Electron-ics Engineering, Vol. 02, Iss. 01, S. No. 001, pp. 1-12, 2021.
A. Houmansadr, S. A. Zonouz and R. Berthier, "A cloud-based intrusion detection and response system for mobile phones," 2011 IEEE/IFIP 41st International Conference on Dependable Systems and Networks Workshops (DSN-W), 2011, pp. 31-32, doi: 10.1109/DSNW.2011.5958860.
G. Portokalidis, P. Homburg, K. Anagnostakis, and H. Bos, “Paranoid Android: Versatile protection for smartphones,” in Proceedings of the 26th Annual Computer Security Applications Conference on - ACSAC ’10, 2010.