Secure Authentication for Banking Using Face Recognition

DOI:
https://doi.org/10.54060/JIEEE/002.02.001Keywords:
Face Recognition, Banking, Security, MySQL, Open CVAbstract
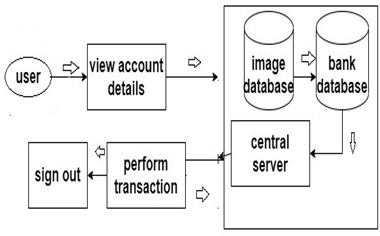
With the increasing demand for online banking lack of security in the system has been felt due to a tremendous increase in fraudulent activities. Facial recognition is one of the numerous ways that banks can increase security and accessibility. This paper proposes to inspect the use of facial recognition for login and for banking purposes. The potency of our system is that it provides strong security, username and password verification, face recognition and pin for a successful transaction. Multilevel Security of this system will reduce problems of cyber-crime and maintain the safety of the internet banking sys-tem. The end result is a strengthened authentication system that will escalate the confi-dence of customers in the banking sector.
Downloads
References
A. Ahmed, J. Guo, F. Ali, et al., “LBPH based improved face recognition at low resolution,” in International Conference on Artificial Intelligence and Big Data (ICAIBD), June 2018.
S. Dumbre, S. Kulkarni, D. Deshpande, et al., "Face Detection and Recognition for Bank Transaction", Journal of Emerging Technologies and Innovative Research (JETIR), vol.3, no. 5, May 2016.
G. Fosse, S. Leo, C. S. Rodriguez, et al., “FEBRABAN survey on Banking Technology”, Technical Report, pp.1-48, 2017.
T. E. Boult, W. Scheirer. " Long-Range Facial Image Acquisition and Quality,” in Advances in Pattern Recognition, London: Springer London, pp.169-192, 2009.
V. Garg, K. Garg, “Face Recognition Using Haar Cascade Classifier”, Journal of Emerging Technologies and Innovative Research (JETIR), vol.3, no.12, pp.140-142, Dec 2016.
Z. Xiang, H. Tan, and W. Ye, “The excellent properties of a dense grid-based HOG feature on face recognition compared to Gabor and LBP,” IEEE Access, vol. 6, pp. 29306–29319, March 2018.
A.A. Falaye , O .OSHO, I. Alabi, et al., “Secure authentication for mobile banking using facial recognition,” IOSR J. Comput. Eng., vol. 10, no. 3, pp. 51–59, 2013.
P. Singhal, P. Sharma, and B. Hazela, “End-to-end message authentication using CoAP over IoT,” in International Conference on Innovative Computing and Communications, Singapore: Springer Singapore, pp. 279–288, 2019.
P. Singhal, P. Sharma, & S. Rizvi, “Thwarting Sybil Attack by CAM Method in WSN using Cooja Simulator Framework, “International Journal of Engineering & Technology, vol.7, no.4.19, pp.589-595 ,2018.
A. Singh and P. Singh,” Object Detection,” Journal of Management and Service Science, vol.1, no.2, pp. 1-20, 2021.
P. Singhal, P. Singh, and A. Vidyarthi,” Interpretation and localization of Thorax diseases using DCNN in Chest X-Ray,” Journal of Informatics Electrical and Electronics Engineering, vol.1, no. 1, pp. 1-7, 2020.
M. Vinny, P. Singh, “Review on the Artificial Brain Technology: BlueBrain” Journal of Informatics Electrical and Electronics Engineering, vol.1, no.1, pp. 1-11, 2019.
A. Sahani, P. Singh, and A. Kumar,” Introduction to Blockchain,” Journal of Informatics Electrical and Electronics Engineering, vol.1, no.1, pp. 1-9, April 2020.
M. Misra, P. Singh,” Energy Optimization for Smart Housing Systems,” Journal of Informatics Electrical and Electronics Engineering, vol.1, no.1, pp. 1-6 April 2020.
N. Srivastava, U. Kumar and P. Singh,” Software and Performance Testing Tools,” Journal of Informatics Electrical and Electronics Engineering, vol. 2, no.1, pp. 1-12, Jan 2021.
F. Abbasi and P. Singh, “Cryptography: Security and Integrity of Data,” Journal of Management and Service Science, vol.1, no.2, pp. 1-9, 2021.
F. Abbasi and P. Singh,” Quantum Cryptography: The Future of Internet and Security Analysis,” Journal of Management and Service Science, vol.1, no.1, pp. 1-12, 2021.
S.K. Tomar and P. Singh, “Cyber Security Methodologies and Attacks,” Journal of Management and Ser-vice Science, vol.1, no.1, pp. 1-8, 2021.